What is the right response and procedure in a cyber emergency? Do you need a specific emergency plan? And is there a correlation between response time and the extent of the damage? In the second part of our interview with Perseus IT forensic expert Julian Krautwald, you will learn what immediate measures companies should take after a cyberattack has occurred.
What would be the proper response and course of action for the affected person in a cyber emergency?
The response and action instructions depend on the incident. In a perfect world, there would be a structured emergency plan for each situation with clearly defined responsibilities and lines of authority that would take effect immediately when a cyber incident occurs. In reality, however, things look different. Here, the right course of action in a cyber emergency depends heavily on the extent to which the affected companies have dealt with incident management (emergency management) in advance.
So what exactly should employees do in an emergency?
Stay calm and don’t panic! They should also be instructed not to decide on their own whether the anomaly or “event” is actually a cyber emergency. In this case, the employee should report the event to the internal IT expert. The IT expert should then investigate the anomaly and decide whether it is a non-safety-critical event (such as a technical problem, user error, service disruption, etc.) or a “real” (for the company) incident. Only then, of course, can further instructions for action be followed.
So there is no one right approach in all cases?
The right course of action in the event of a cyber emergency depends, of course, on the extent to which the company concerned has already dealt with the issue of incident management and the extent to which this work has resulted in the creation and issuance of corresponding guidelines and clear processes or instructions for action for the employees. It already starts with the fact that most companies have not even defined for themselves what is an information security incident for the company itself and what may only be a technical problem. In other words, there is no one-size-fits-all course of action in a cyber emergency, because while one course of action may be exactly right for one company, it could make the emergency worse for another.
Is there a correlation between response time and the extent of damage?
There are incidents where the resulting impact actually depends on the response time. For example, is “only” one of my systems encrypted or an entire network and my backups as well? Are “only” a few “unimportant” data exfiltrated or over hundreds of GB of highly sensitive trade secrets?
Are “just” a few acquaintances attacked with phishing mails via the infected e-mail server “in my name”, or is it the entire address book of the company with all business contacts?
All these examples demonstrate that a fast, but above all coordinated and considered approach to handling cyber emergencies can limit the expected damage enormously.
What measures should be implemented promptly by companies that have not yet integrated a sustainable cybersecurity culture into their operations?
Anchoring a cybersecurity culture in a company is not something that can be done overnight, of course – it is much more of a lengthy process. In addition, it is of course important not to make this a one-off event, but to integrate and live the topic of information security in the long term. Whether you are trying to integrate a cybersecurity culture into your company that is as deeply rooted as possible, or whether you want to start with a few short-term measures, there is one thing you cannot avoid: The topic of information security must be made a top priority. If the management does not focus on the topic and does not recognize its importance, a company will find it extremely difficult to really achieve anything.
How do you derive which short-term measures are the right ones for your company?
First, it certainly makes sense to think about how long you can actually “survive” without access to certain of your company’s data or systems, or how serious it would be if certain sensitive information were to fall into the hands of unauthorized third parties. In other words, you should first identify your “crown jewels” and then take the next step to secure them with appropriate measures.
A minimal plan of action for securing workplace computers could thus consist of the following topics, for example:
- Secure passwords
- 2-factor authentication
- Use of anti-virus software and firewalls
- Software updates
- Handling incoming e-mails and securing outgoing e-mails
- Restriction of rights (principle of least privilege)
- Creation and protection of security copies (backups)
In addition, it makes sense in any case to create an emergency plan – that is, to think about a process of who does what and how exactly in a cyber emergency. If clear responsibilities are also assigned in this step, you can save a lot of time and, at the end of the day, a lot of money in the event of a cyber emergency.
Incident types and immediate actions
A selection of possible cyber incidents:
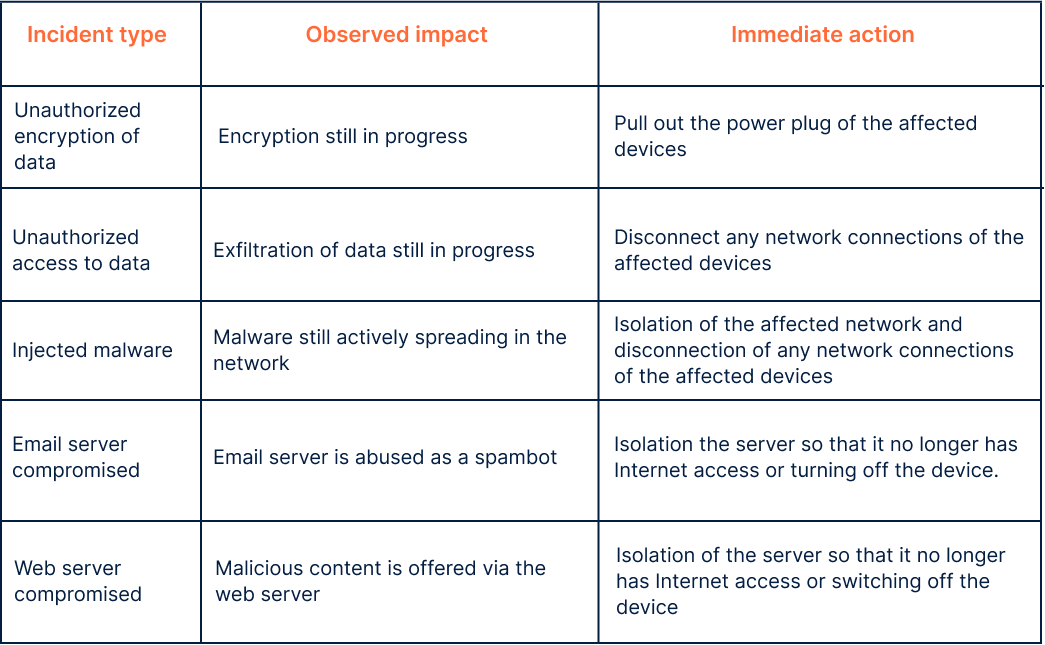
Pic Source: Perseus Technologies GmbH
