In the past few days, there has been increasing information that malware attacks on German companies are on the rise. Furthermore, the research team from security software vendor Kaspersky discovered a new type of dangerous bootkit that still raises questions. In the following article we will tell you what exactly has happened, who is at risk and how you can protect yourself.
German companies increasingly attacked with “Hyberbro” malware
In its Cyber letter 01/22, the German domestic intelligence services warn of an ongoing espionage campaign by the group APT 27. According to them, this acronym stands for a Chinese group of criminal hackers, also known as “Emissary Panda”, who has already been blamed for cyberattacks on Western government agencies in the past.
It is said that attackers use a remote access trojan (RAT) called “Hyberbro”. A RAT is a malware program that opens a backdoor for administrative control on the target system. RATs are usually downloaded in the background by a program invoked by the user. In the current case, it is suspected that the malware was installed on countless computers by exploiting vulnerabilities in the password management program AdSelfService Plus1 from the Indian software manufacturer Zoho. The vulnerability in Microsoft Exchange, which became known back in March 2021, is also seen as a gateway for “Hyberbro”, as many companies have still not closed the gap.
This type of cyber attack focuses primarily on the theft of trade secrets and intellectual property. However, the German domestic intelligence services do not rule out the possibility that the attackers could also infiltrate the networks of customers and service providers through this and compromise several companies at once accordingly.
For experts: Possible indicators of infection
The Cyber letter also contains information on how to detect an infection with “Hyberbro”. Among the Indicators of Compromise (IOC), three IP addresses are listed that the RAT seeks to contact:
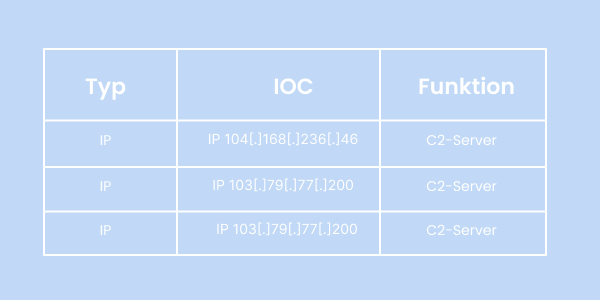
Furthermore, certain files, paths or processes may also indicate an infection. You can find all details in the Cyber letter 01/22 of the Federal Office for the Protection of the Constitution.
What you can do
We advise admins and IT managers:
- Install all security updates to close vulnerabilities.
- Check your own systems for indications from the listing of the Federal Office for the Protection of the Constitution.
- Isolate and clean up compromised systems if necessary or contact your IT service provider.
- Use Intrusion Detection System (IDS). This attack detection system is an addition to the existing firewall, but it can also run directly on the computer being monitored, increasing the security of networks and computer systems. Your network firewall provider can help you here.
Security professionals identify new bootkit “MoonBounce”
Furthermore, security researchers of Kaspersky have found a new type of dangerous bootkit called “MoonBounce” on a customer’s computer. A bootkit is a malicious program that nests in the motherboard and spreads through the Unified Extensible Firmware Interface (UEFI). The UEFI serves as an interface and contains information that is used on the computer to load the operating system.This means that the contained malicious code is executed even before the operating system boots up.
This way, MoonBounce manages to bypass most security mechanisms and control the start of the operating system unnoticed, as well as modify the system code and drivers before antivirus and other security components are loaded.
If a computer becomes infected, either the SPI error memory must be reloaded or the entire motherboard must be replaced.
It is currently unclear how the device became infected with “MoonBounce”. However, it is suspected that this was done remotely. Since the development of a bootkit like MoonBounce is a rather complex matter, for which conventional cybercriminals have hardly any resources, it is suspected that the targets are mainly economic and governmental. Based on the characteristics of the malware, Kaspersky experts have suspected a team in the context of MoonBounce, which is referred to as ATP41 and is believed to originate from China.
What you can do
- Activate Secure Boot by default: The program prevents viruses, worms or rootkits from manipulating the PC and causing damage. If manipulation is detected, the PC simply does not start. Manipulations by users are also made more difficult.
- Update the firmware regularly
